Your Authentication Dashboard
The Credentials Breakdown filters consider hosts scanned in the last 30 days only. View record details to see when each host was last scanned using authentication.
Use the Credentials Breakdown to quickly filter your records list to show:
- Credentials that have not been attempted in the last 30 days (Unused)
- Credentials that were successful 100% of the time (Passing)
- Credentials that were not successful for some of the hosts in the record (Problematic)
- Credentials that were not successful for more than 50% of the hosts in the record (Failing)
- Credentials stored in a password vault (In Vault)
Tip - You can also search for records by type, network, title, IP address and vault type.
Authentication status for each hostAuthentication status for each host
Drill down into record details to see pass/fail authentication status for your scanned hosts. The Updated column shows you when each host was last scanned using authentication - this is when the status was last updated.
Pass - Authentication to the host was successful.
Fail - Authentication to the host was not successful. Please refer to the Cause column for more information like the credentials used in the authentication attempt.
Not Attempted - Authentication to the host was not used (not counted as pass or fail). Perhaps you've never scanned the host using authentication or you did but the host scan data was purged. Please note - If you're in VM, we're looking at vulnerability scan data. If you're in PC, we're looking at compliance scan data. Let's say you scanned a host in PC using authentication but you didn't scan it in VM using authentication. You'll see a Pass/Fail status in PC and Not Attempted in VM.
Search authentication recordsSearch authentication records
Use the Search option at the top of the Authentication page to quickly find authentication records by different criteria like title, network, record type, IP address, modified date, and more.
Click ![]() to see the search options available, make your selections and then click Search again. You can also simply start typing in the Search field to find a search category and then provide a search value.
to see the search options available, make your selections and then click Search again. You can also simply start typing in the Search field to find a search category and then provide a search value.
Click  to clear the Search field and show all records.
to clear the Search field and show all records.
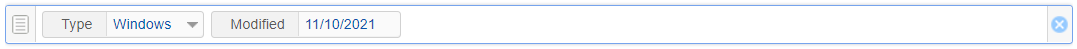
When searching by Modified date, please note that the search will look for records with a modified date less than the date entered. It does NOT search for records equal to the date entered. For example, if you select a Modified date of 11/10/2021, then we will return records modified before this date. We will not return records modified on this date.
Download authentication listDownload authentication list
You can download any data list within the UI in order to view your configurations outside of the product. Learn more.