Cloud perimeter scans use Qualys External Scanners (Internet Remote Scanners), located at the Qualys Cloud Platform. For subscriptions on Private Cloud Platforms, your account may be configured to allow internal scanners to be used. Contact Qualys Support or your Technical Account Manager to have this option enabled for your subscription.
Cloud perimeter scans are DNS or IP -based scans launched using the public DNS or Public IP of the target instances. If both public DNS and public IP address exist for your assets, then we will launch a scan on public DNS.
These scans are supported in VM/VMDR for vulnerability scanning and PC/SCA for compliance scanning.
You'll need to have these features enabled for your account: Cloud Perimeter Scanning, EC2 Scanning, Scan by Hostname.
Your account must have a Manager or Unit Manager role.
EC2 connector is required. Learn more about connectors.
You need to configure this same EC2 connector in your CloudView account if you wish to include public load balancers from the connector in the scan. To create the connector, your account must have CloudView subscription and your platform has access to CloudView base URL "qweb_cloud_view_base_url". See "Configure Your AWS Connector" in the CloudView Online help.
If you wish to include micro, nano and small instance types in the scan, these instance types should be activated for your account.
Looking for an overview on securing your Amazon AWS infrastructure? Go here.
You'll need to have these features enabled for your account: Cloud Perimeter Azure VM Scan, Cloud Perimeter Scanning, EC2 Scanning, Scan by Hostname.
Your account must have a Manager or Unit Manager role.
Azure connector is required. Learn more about connectors.
All cloud perimeter scans are scheduled - either for "now" (a one-time scan job) or "recurring". Once saved, you’ll see the scan job on the Schedules list. When the scan job starts it will appear on your Scans list.
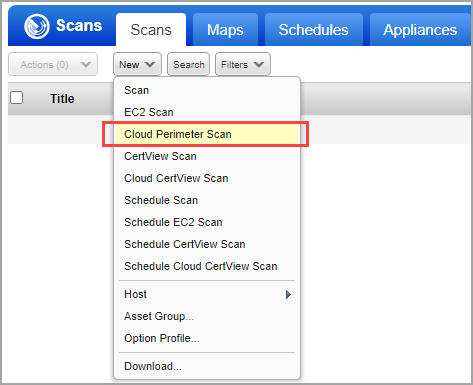
Go to the Scans tab and choose New > Cloud Perimeter Scan. You'll also see this option on the Schedules tab.

The first thing you'll do is pick your cloud provider - Amazon Web Services or Microsoft Azure. (The Microsoft Azure option is only shown when "Cloud Perimeter Azure VM Scan" is enabled. See requirements above.)

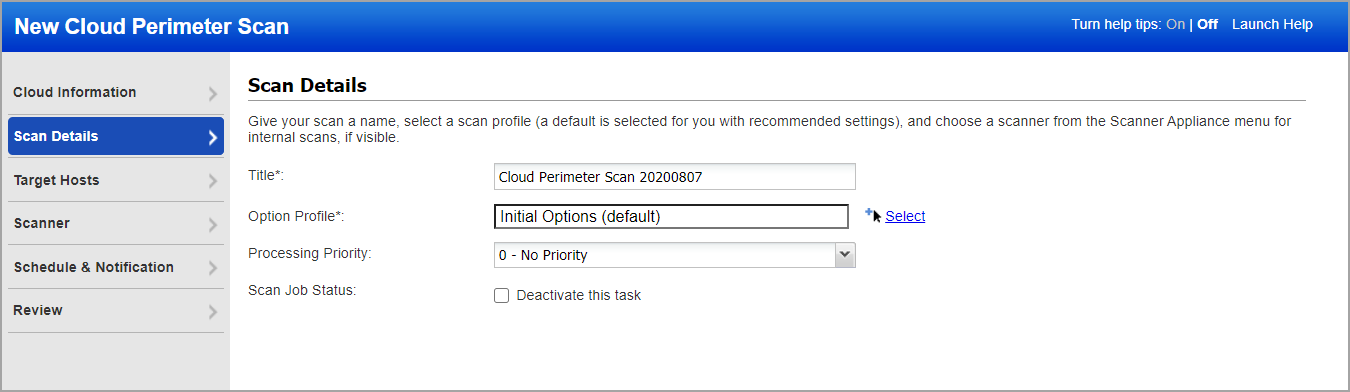
Give your scan a title and select the option profile you configured with authentication.
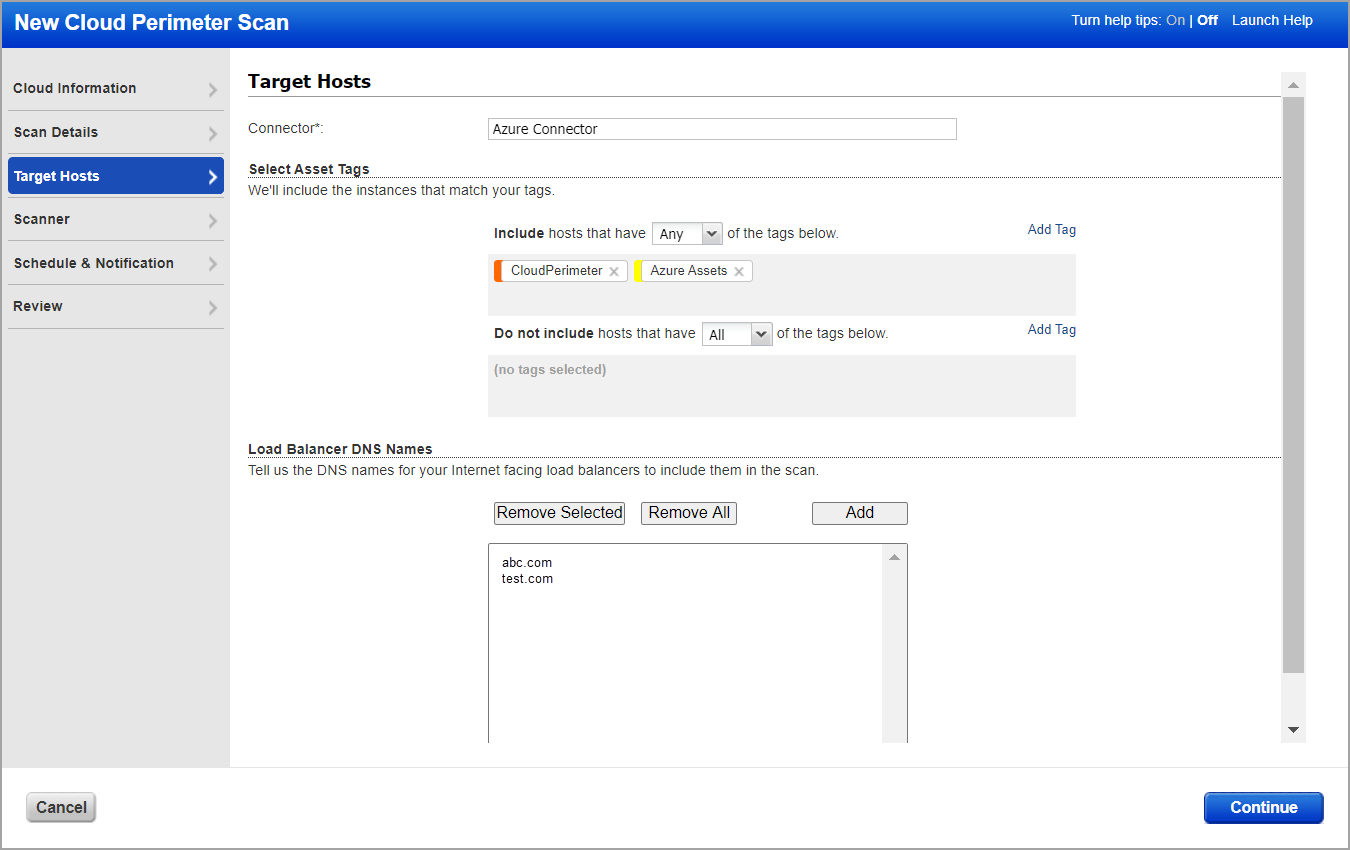
Now it's time to pick your connector and target hosts. The options you see will differ depending on the cloud provider you selected.
For AWS EC2
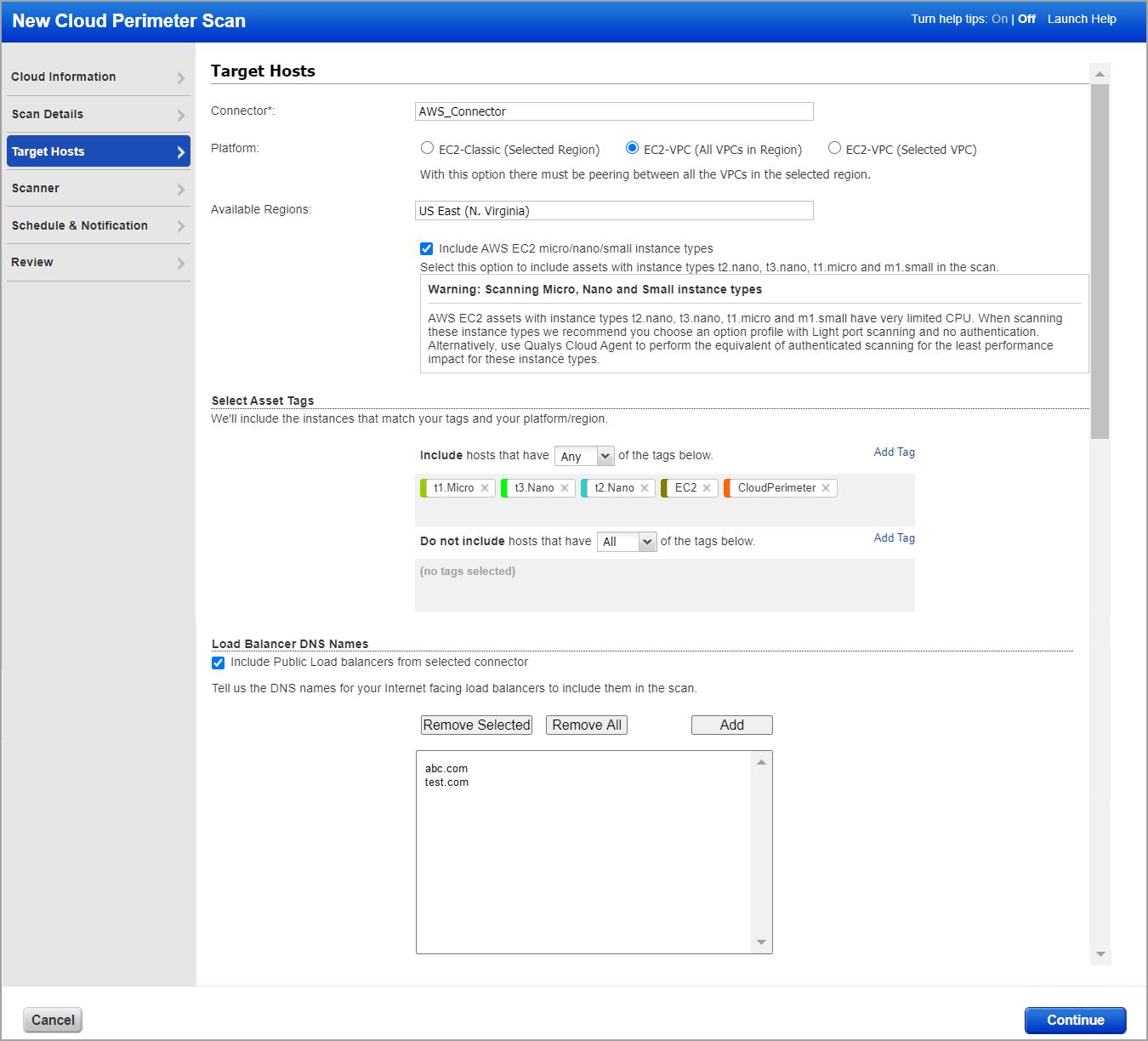
Make target host selections. Note that if you do not specify the platform, region code, vpc id, asset tags or load balancer DNS names, then we will launch the scan on the assets resolved from the connector.
- (Required) Select the EC2 connector you configured.
- (Optional) Choose a platform option - EC2 Classic, EC2 VPC (All VPCs in region) or EC2 VPC (Selected VPC). Based on your selection you’ll select region(s).
- (Optional) You have the option to include assets with instance types t2.nano, t3.nano, t1.micro and m1.small in the scan. When you select this option, we will show you a warning message recommending you to perform no authentication, light port scanning for these instances types. Note that to include micro, nano and small instance types in the scan, these instance types should be activated for your account.
- (Optional) Select asset tags. These are assets activated for your connector.
- (Optional) See "Requirements for AWS EC2" above to know if this option is available. If available, select the "Include Public Load balancers from selected connector" option and we'll fetch public load balancers from the AWS connector in CloudView with the same configuration as that of the selected connector. If you select this option, ensure that you have the connector created in your CloudView account with a configuration similar to that of the selected connector. If the connector in CloudView is not found, then selecting this option won't fetch any public load balancers. See "Configure Your AWS Connector" in CloudView Online help. (Note - EC2 Classic platform does not support public load balancers.)
- (Optional) Enter DNS names of your load balancers to include them in the scan along with public load balancers. Click Add to manually enter the DNS names.
For Azure VM
Make target host selections. Note that if you do not specify asset tags or load balancer DNS names, then we will launch the scan on the assets resolved from the connector.
- (Required) Select the Azure connector you configured.
- (Optional) Select asset tags. These are assets activated for your connector.
- (Optional) Enter DNS names of your load balancers to include them in the scan. Click Add to manually enter the DNS names. Note that for Azure VM scan, we do not support pulling load balancer DNS names from the Cloud View module.
By default cloud perimeter scans use Qualys External Scanners.
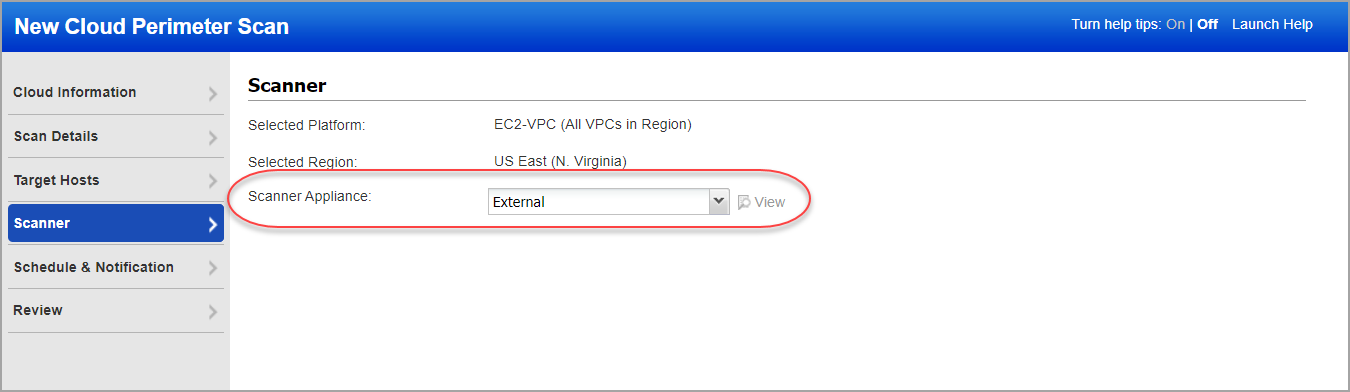
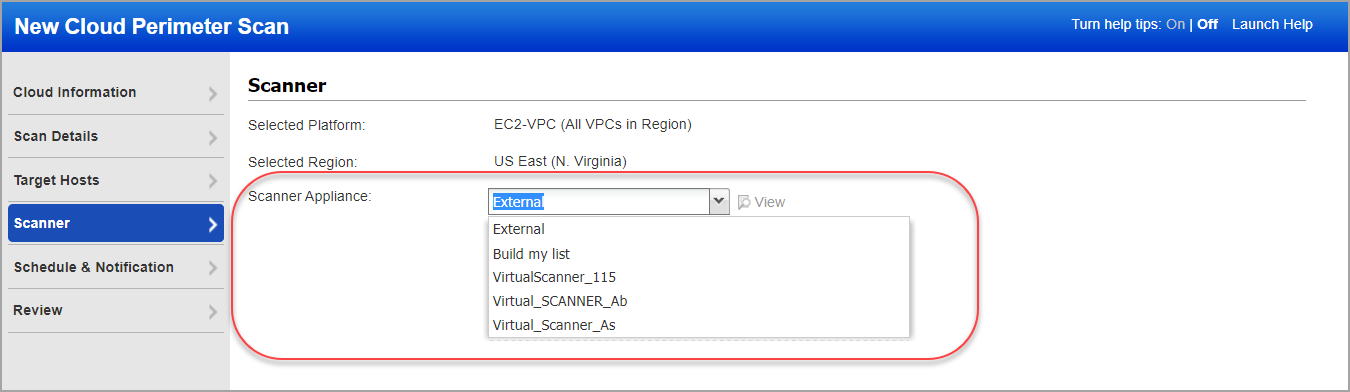
For Private Cloud Platforms - Your subscription may be configured to allow scanner appliances to be used for cloud perimeter scan jobs. In this case, choose one or more scanner appliances from the list (use the Build my list option).
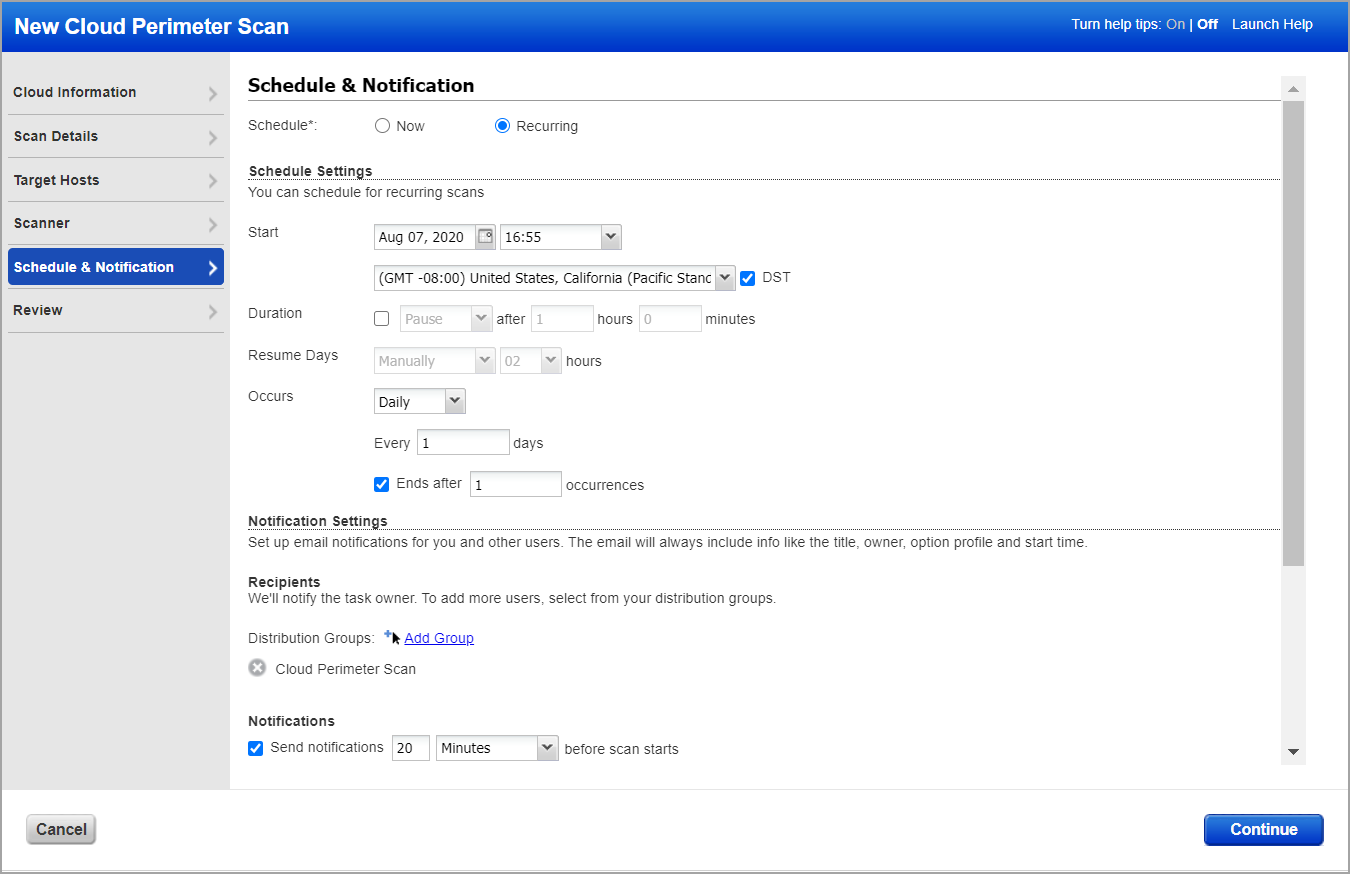
Tell us when you want the scan to run - Now or Recurring.
Note that when you choose Now your scan may not start immediately. We'll check for new scan requests every few minutes. If a scanner is available and you haven't reached your concurrent scan limit then we'll launch the scan. If scanners are not available or you have reached your limit then the scan will be launched at the next opportunity.
When you choose Recurring you'll also set scheduling and notification options. These are the same settings as other scan schedules so they should look familiar.
We’ll identify the assets to scan based on your settings.
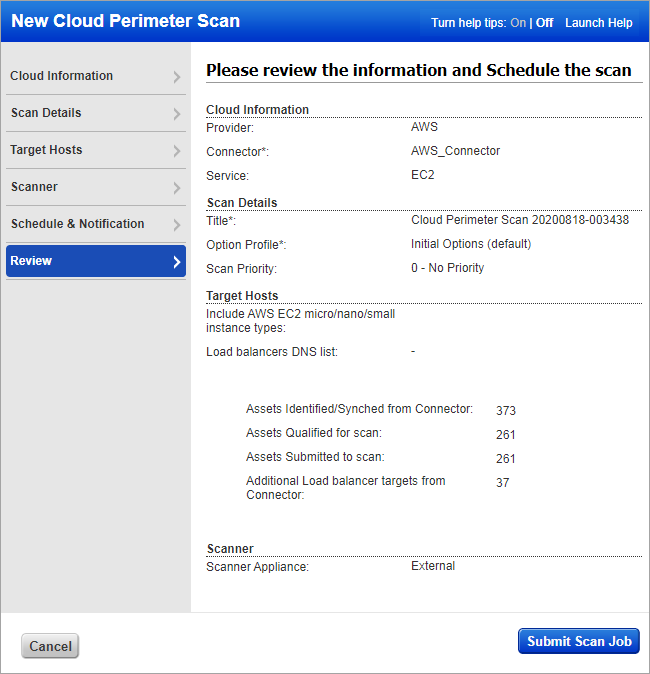
For AWS EC2
For Azure VM
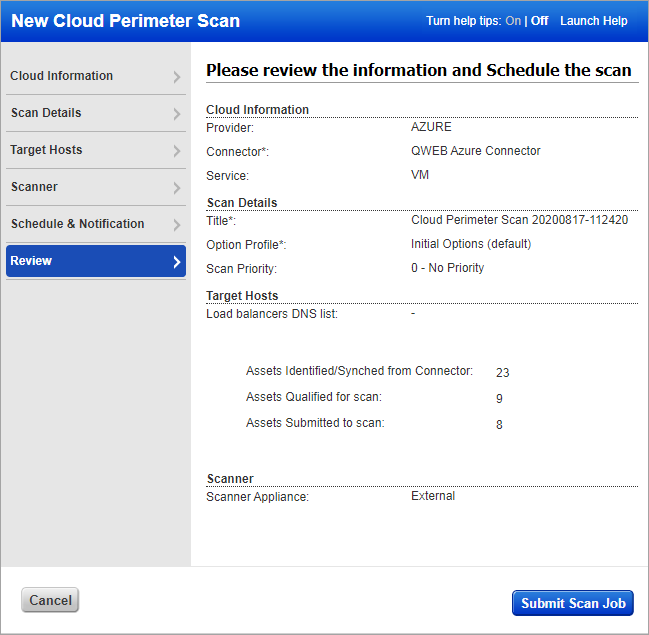
You’ll see these asset counts:
Assets Identified / Synced - The number of assets discovered by the connector that you selected for this scan job.
Assets Qualified for scan - The number of assets discovered by the connector that also match the selected platform and region (EC2) and asset tags (Azure and EC2). For EC2, if you chose to include micro/nano/small instances, then we will add the count of these instances in the total count of assets qualified for scan. We’ll remove the Terminated instances.
Assets Submitted to scan - The number of assets that we’ll submit in the scan job. For EC2, if you chose to include assets of instance types micro/nano/small, then this number will also include the count of these instances. We start with the qualified assets (previous count) and filter out assets that are not activated for VM (for vulnerability scan) or not activated for PC (for compliance scan).
Additional Load balancer targets from Connector - The number of public load balancers discovered by the selected connector.
After reviewing the settings and confirming the asset count, click Create Scan Job.
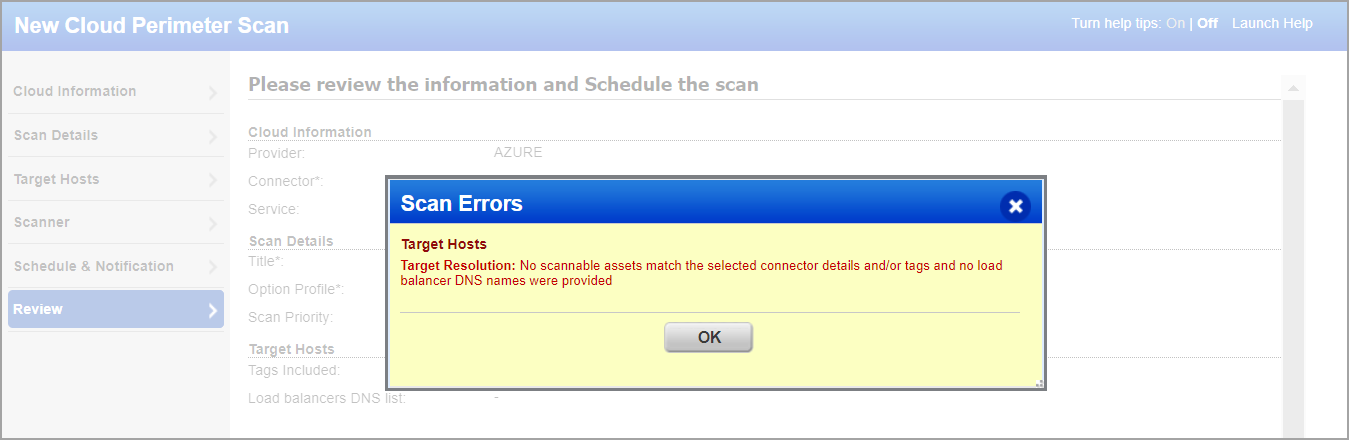
When submitting a scan job, a warning message that "no scannable assets are found" is shown 1) if no assets and public load balancers are resolved from the connector and for the optional "platform" and "asset tags" selections and 2) if no load balancer DNS names are provided. Click OK to proceed with submitting the scan job. You can find such scan jobs under Scans > Schedules tab.
Your new scan job will appear on the Schedules list.
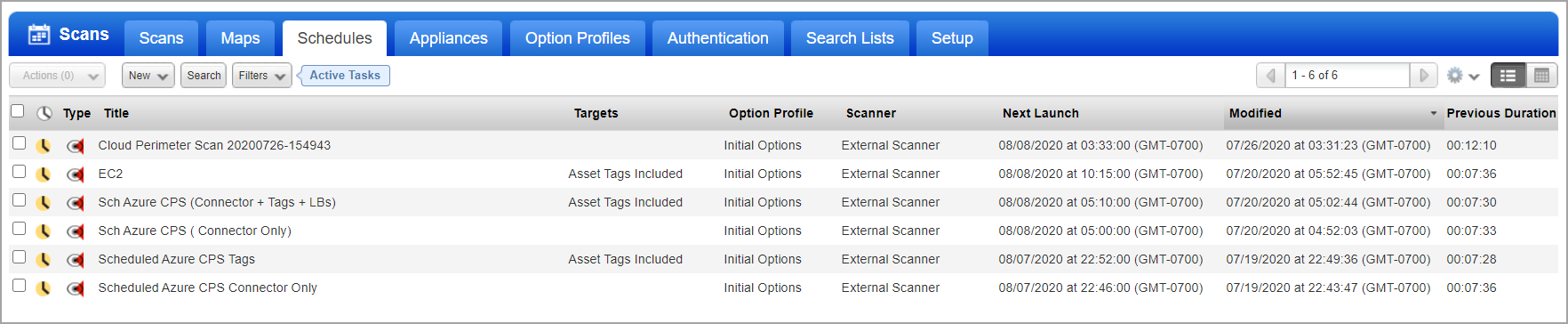
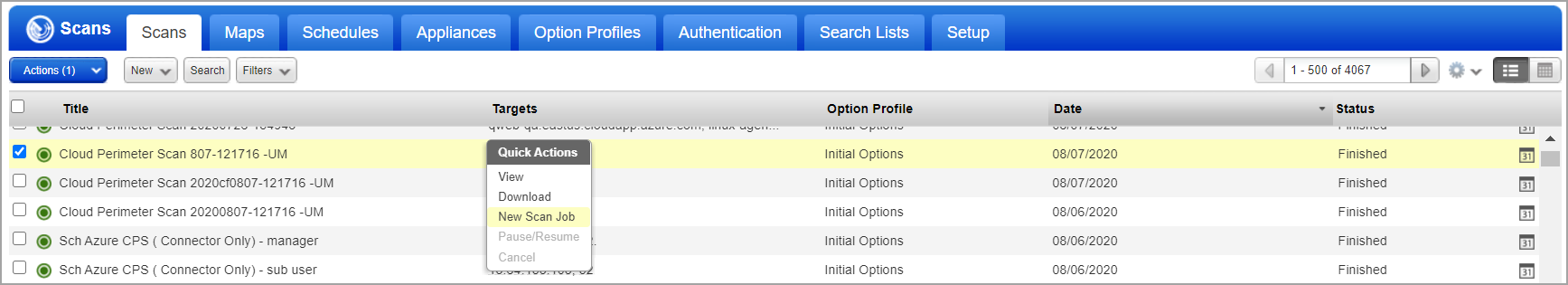
When your scan starts it will appear on the Scans list. Like with other scans you can take actions like cancel or pause the scan, view the scan status and download the results.
Want to run the scan again? Choose New Scan Job from the Quick Actions menu. We’ll retain certain scan settings from the original scan job and schedule the scan to run "Now”.